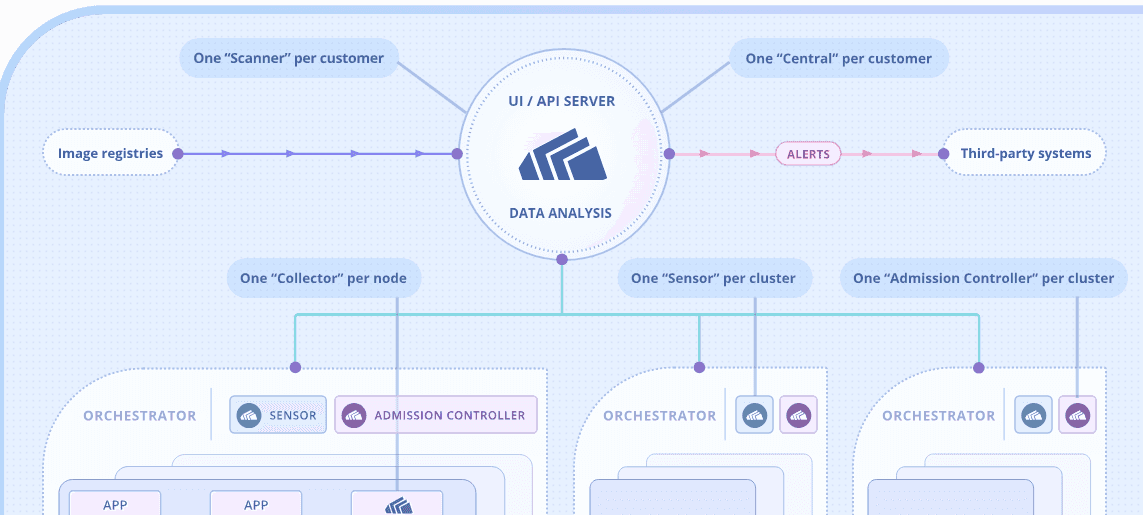
With the launch of StackRox 4.6, the StackRox team is excited to introduce a new integration with Microsoft Sentinel. In this post, we’ll walk you through how to configure StackRox to send events to a Microsofts Azure Log Analytics Workspace and respond to these events within Microsoft Sentinel.
Disclaimer: This article will not cover the basics of Microsoft Sentinel or SIEM platforms.
Requirements
Microsoft Azure Requirements
To send StackRox alerts and audit logs to Microsoft Sentinel, you first need to configure the Azure instance to include the following resources:
- Data Collection Rule
- Data Collection Endpoint
- Log Analytics Workspace
- Service Principal
Sentinel does not need to be created separately; it will always be usable. This guide will use secret authentication for the Service Principal.
StackRox Requirements
- A StackRox user with write permissions for integration resources.
How to Create the Azure Resources
You can use the Terraform scripts in the StackRox contributions repository to create Azure resources. The contributions repository is community-driven and contains many useful StackRox and security resources. It is not officially supported.
You can find the Terraform script here: StackRox Contributions Terraform Scripts
How to Create the StackRox Notifier
To create the notifier, export the following data to grant StackRox access to the Azure Log Analytics Workspace:
export LOG_INGESTION_ENDPOINT="log-ingestion-endpoint.com"
export DIRECTORY_TENANT_ID="tenant-id"
export APP_CLIENT_ID="app-client-id"
export SECRET="secret value"
export DATA_COLLECTION_RULE_ID="data collection rule id"
export STREAM_NAME="Custom-stackrox_alerts_CL"
export ROX_API_TOKEN="api-token"
export ROX_ENDPOINT="https://localhost:8000"Send a POST REST request to the StackRox notifier’s API endpoint:
notifier=$(cat <<EOF
{
"name": "sentinel-notifier",
"uiEndpoint": "localhost:8000",
"type": "microsoftSentinel",
"microsoftSentinel": {
"logIngestionEndpoint": "$LOG_INGESTION_ENDPOINT",
"alertDcrConfig": {
"dataCollectionRuleId": "$DATA_COLLECTION_RULE_ID",
"streamName": "$STREAM_NAME",
"enabled": true
},
"auditLogDcrConfig": {
"dataCollectionRuleId": "$DATA_COLLECTION_RULE_ID",
"streamName": "$STREAM_NAME",
"enabled": true
},
"directoryTenantId": "$DIRECTORY_TENANT_ID",
"applicationClientId": "$APP_CLIENT_ID",
"secret": "$SECRET"
}
}
EOF
)
curl -k "$ROX_ENDPOINT/v1/notifiers/test" \
-X POST \
--data "$notifier" \
-H "Authorization: Bearer ${ROX_API_TOKEN}" \
-H "Content-Type: application/json"Configure a Policy to Send Alerts to Sentinel
Trigger an alert using the “Latest Tag” policy:
- Navigate to Platform Configuration > Policy Management.
- Edit the “Latest” tag policy.
- Under Policy Behavior > Actions, select the previously created “sentinel-notifier.”
Trigger a Violation: Deploy an Image with the “Latest” Tag
To trigger a violation:
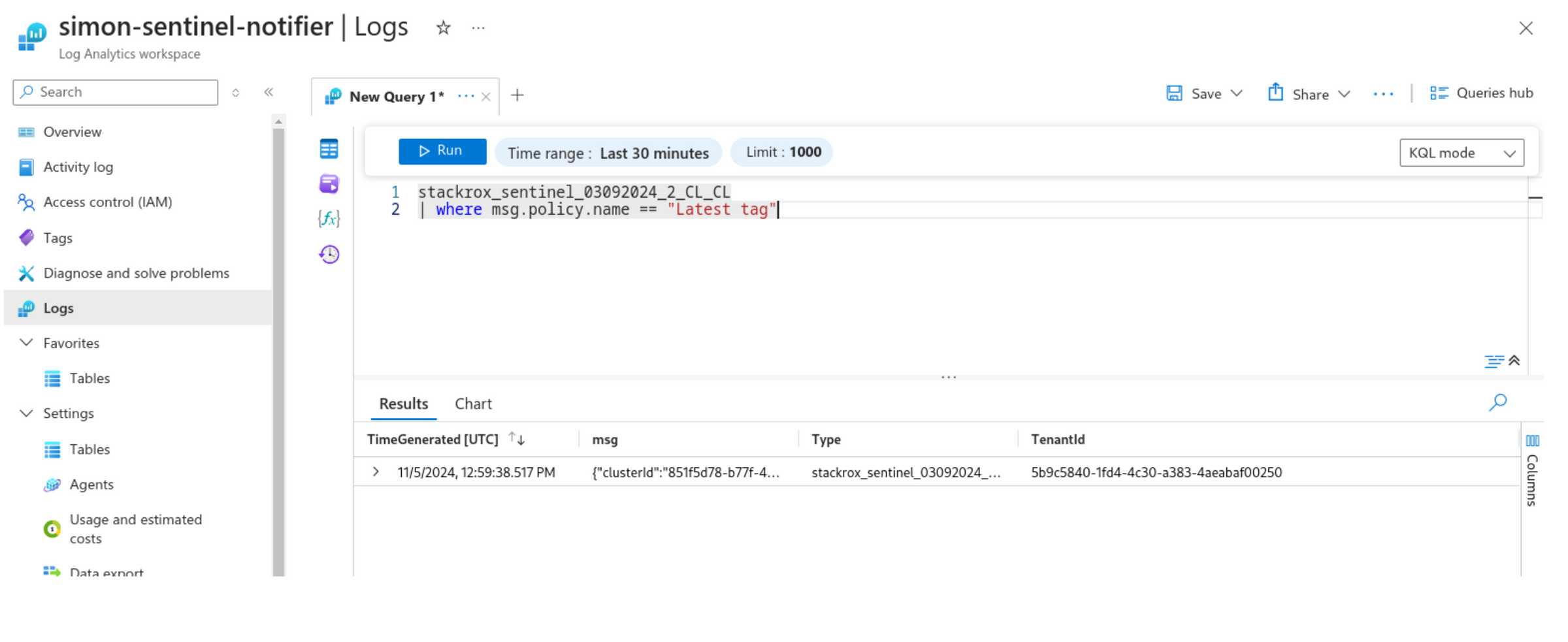
kubectl -n <namespace> create deployment nginx --image=nginx:latestAfter creating the deployment, StackRox should generate a new alert and send it to the Azure Log Analytics workspace. To verify, run the following KQL query in Azure:
Custom-stackrox_alerts_CL
| where msg.policy.name == "Latest tag"When creating the Scheduled query rule, the wizard should look like this:
Create Microsoft Sentinel Alerts
With StackRox alerts, you can configure Microsoft Sentinel to create incidents using KQL queries automatically:
- Navigate to Microsoft Sentinel > Analytics > Create > Scheduled Query Rule.
- In the “Set Rule Logic” section, input the KQL query provided above.
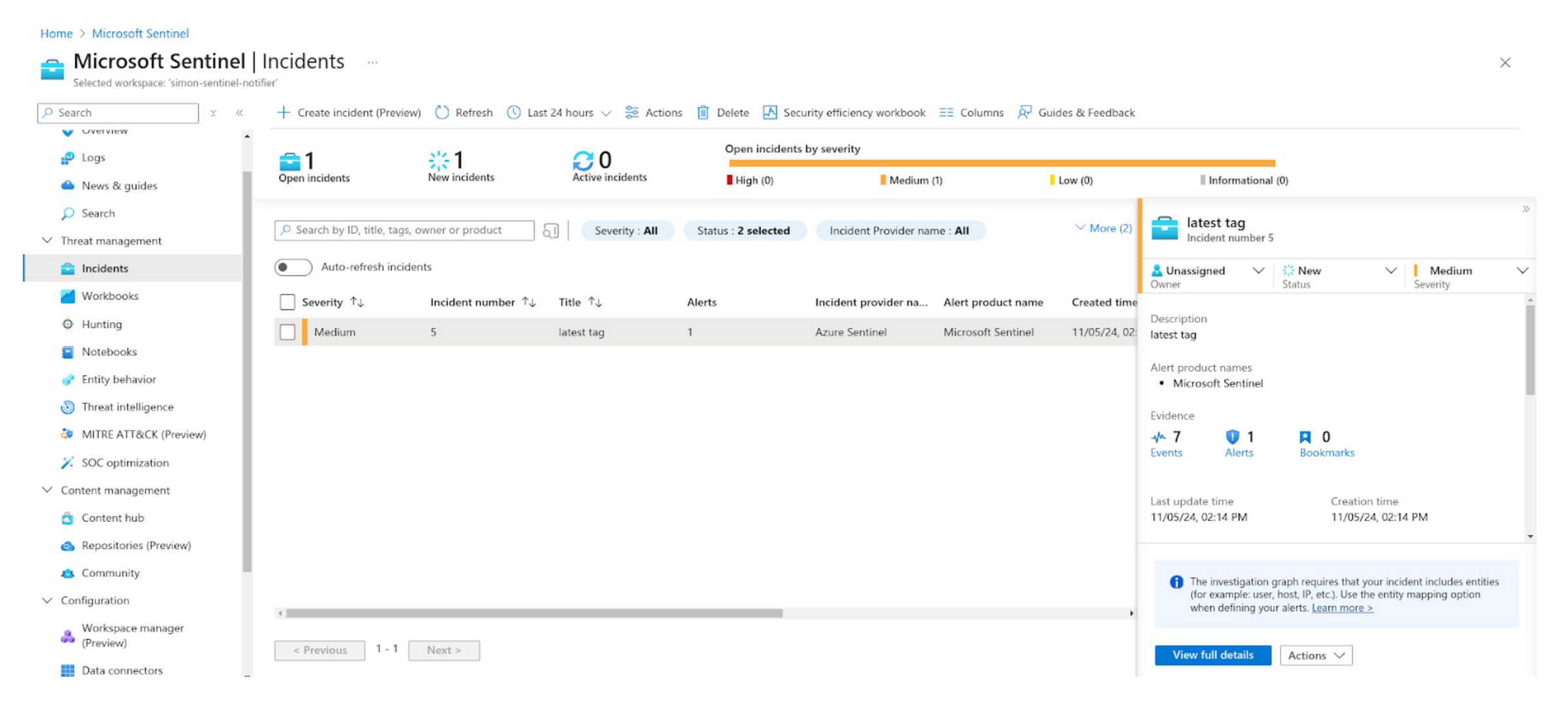
Validate the query by navigating to Microsoft Sentinel > Threat Management > Incidents. Look for an incident labeled “Latest” tag.
Conclusion
This post demonstrates how to integrate StackRox alerts with Microsoft Sentinel and automate incident creation using KQL queries. This integration streamlines security operations and enhances incident response workflows.